Today, 81% of enterprises use at least one cloud-based application or have at least one segment of their computing infrastructure in the cloud. And the rate of cloud adoption has significantly risen due to the global health crisis. According to a recent survey from Flexera, 27% of leaders mentioned a significant increase in cloud spending due to Covid-19.
What Is the State of Cloud Security Today?
The cloud and digital transformation have radically changed the IT landscape and introduced new threats and security requirements. The Shared Responsibility Model for Cloud has relieved organizations from the burdens of securing physical IT infrastructure, which is now the responsibility of the Cloud Service Providers (CSPs) such as Amazon Web Services, Microsoft Azure, and Google Cloud.
However, the most significant portion of responsibility today is on the cloud customer. According to Gartner, through 2023, at least 99% of cloud security failures will be the customer's fault, mainly in the form of cloud resource misconfiguration.
Many of the data breaches that make the headlines resulting from the exploitation of cloud misconfiguration mistakes.
The Most Common Challenges Organizations Face With Cloud Security
Misconfugirartion is the number one risk for any organization. And what makes it so hard to manage is the fact that it's born of many causes. However, you can attribute all of those causes to different kinds of human error.
Let's take a look at the report conducted by Fugue. The company surveyed 300 cloud professionals, including cloud engineers, cloud security engineers, DevOps, and cloud architects.
They've found that the top 3 causes of cloud misconfigurations are:
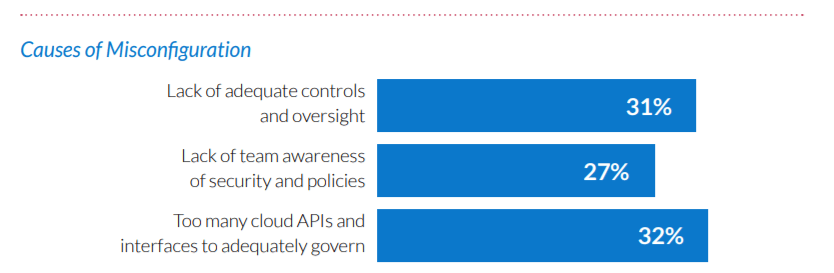
Other causes of cloud misconfigurations include:
- Lack of adequate monitoring of the cloud environment
- Lack of cloud security expertise in teams
- Negligent insider behavior
- Not checking the infrastructure as code before deployment
So, here's how cloud customers get security wrong. What can you do about it?
How to Improve Your Cloud Security in 2023
Security has always been about standards, guidelines, and protocols tried and tested over the years. But if organizations try to cut corners or ignore basic security principles (i.e., insufficient logging and monitoring of unauthorized and malicious activities), that's like an invitation to intruders.
Data increases the value of the business. And as a result, it becomes a target for cyberattacks. But attackers' methods go from pretty standard: phishing, malware distribution, impersonating legitimate domain names, stolen account data, attacking remote access, cross-site scripting, and identity theft.
Don't Overdo Your Security
There is such a thing as too much security. For example, let's say that your CSP offers a plethora of audit trails, logs and metadata you can collect. Tempting, right? But as soon as you enable all the features available, the information flow will sweep you off your feet.
Understand what's normal for your environment. That way, it will be easier to spot any suspicious activities as you analyze your logs. You might also want to introduce some cloud-native configuration state monitoring tools to complement your log analysis application. Otherwise, you might miss a sign of an actual attack in the flood of irrelevant security events.
Understand And Regularly Audit User Identities and Cloud Inventory
The visibility of your cloud environment should be clear as water. Meaning that you should have a bird's eye view of how everything's configured and who has access to what. Moreover, with the proper visibility, you should be able to track the changes, who made them, and what it looked like before. User identities (human or non-human) should be part of the inventory.
Let's put this into perspective. Just like there's an onboarding process, there should be an established offboarding process too. Learn it from Cisco's mistakes.
Implement MFA and Use Strong Passwords
The traditional username/email and password combo no longer cut it. And don't even think about using the "password" password and the same password for multiple services/accounts.
Once the hacker has user credentials, they can access any apps you use to run your business. Implementing Multi-Factor Authorization (MFA) is one of the easiest and cheapest ways to add an extra layer to security. As a result, it has become a standard. For instance, PCI DSS v3.2. requires you to secure all individual non-console administrative access and all remote access to the CDE using multi-factor authentication. PCI DSS v4/o reinforces this.
Keep in Mind the Regulations
Remember The Shared Responsibility Model for Cloud? It states that security and compliance is a shared responsibilities between the CSP and the customer. So, if you're building or upgrading your cloud environment, we highly recommend you pay attention to the regulations that may apply to you. But, again, let's put this into perspective. Say your CSP is compliant with GDPR. Whatever solution you build on top of it may not be. It is your responsibility to configure your environment, so it's compliant with a given regulation.
Moreover, certain countries and industries have strict regulations on storing and processing data about their citizens. So, keep that in mind as well.
What's the Future of Cloud Security?
The Internet has many thoughts and expert opinions about how cloud computing and security are going to develop. However, one thing is for sure: the world has shifted to remote work. In 2023, we will undoubtedly see a continuation of rapid cloud adoption and growth.
Hence, the approaches and methods of cloud security will improve from the perspective of infrastructure providers and organizations. Organizations will deploy and improve security strategies covering app and network-level firewalls, DDoS prevention defences to prevent malware and cyber attacks. Secure product is a must for those companies who want to meet customer requirements and stand up to the competition on the market.


