In a significant milestone for data security and customer trust, Help Desk Migration has successfully achieved SOC 2 Type II and SOC 3 compliance. This achievement marks an essential addition to Help Desk Migration’s security portfolio, reinforcing the company’s commitment to maintaining the highest standards of data security. SOC 2 Type II and SOC 3 compliance assures customers that their data is handled with the utmost care, and adds a robust layer of security to Help Desk Migration’s already comprehensive security measures.
What is SOC 2 Compliance?
SOC 2, which stands for System and Organization Controls 2, is an auditing procedure developed by the American Institute of CPAs (AICPA). It evaluates organizations based on five "trust service criteria": security, availability, processing integrity, confidentiality, and privacy.
Achieving SOC 2 Type II compliance means that Help Desk Migration has been rigorously assessed and found to adhere to these stringent standards. This ensures that our migration services are designed to keep customer data secure and private.

What is SOC 3 Compliance?
SOC 3, or System and Organization Controls 3, is a public report that highlights how a service organization protects data through security, availability, processing integrity, confidentiality, and privacy. It follows the same Trust Services Criteria as SOC 2 and includes the auditor’s opinion, system description, and management’s assertion. SOC 3 reports always cover a specific period, making them Type II by default.
Unlike SOC 2, SOC 3 doesn’t include detailed test results. Organizations use it to build trust, support marketing efforts, and publicly demonstrate their commitment to strong security practices without disclosing sensitive audit information.
Strengthening data migration security
Data migration involves transferring data between different help desk or service desk systems, formats (i.e., CSV files, databases,) or storage environments, which can be a highly complex and sensitive process.
The attainment of SOC 2 Type II and SOC 3 compliance signifies that the Help Desk Migration service has implemented robust security measures to protect data during every phase of the migration process. This includes advanced encryption techniques, secure data handling protocols, and rigorous access controls.
Our SOC 2 Type II and SOC 3 compliance guarantees that our customers' data is shielded from unauthorized access, breaches, and other potential threats.
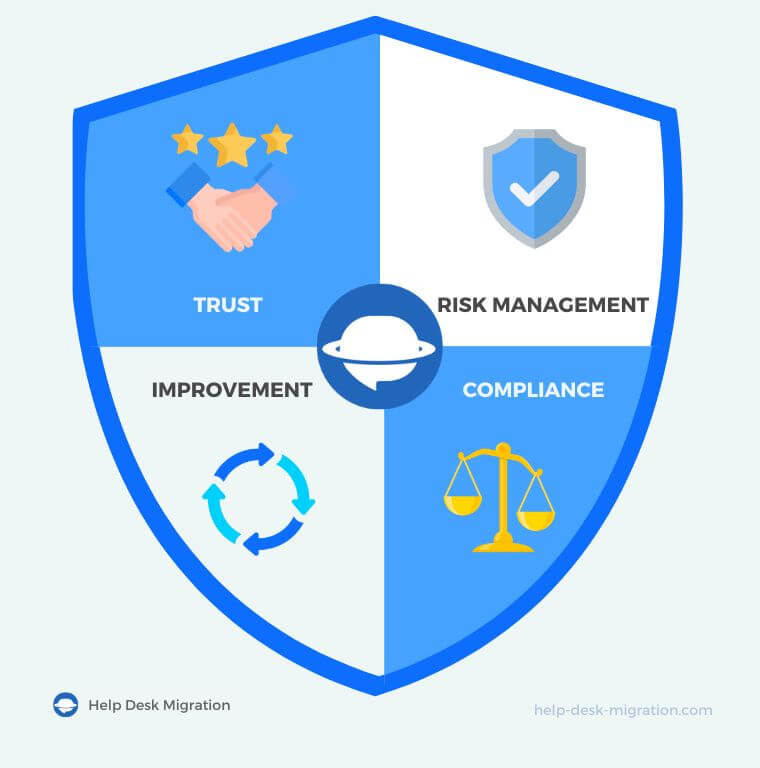
4 benefits for Help Desk Migration customers
Enhanced trust and confidence
For our customers, SOC 2 Type II and SOC 3 compliance translates into enhanced trust and confidence. Knowing that Help Desk Migration adheres to the highest standards of data security reassures clients that their sensitive information is in safe hands. This is especially crucial for businesses that deal with large volumes of personal and confidential data, such as healthcare providers, financial institutions, and tech companies.
Superior risk management
Achieving SOC 2 Type II and SOC 3 compliance demonstrates that Help Desk Migration has a proactive approach to risk management. Our comprehensive security protocols not only prevent data breaches but also ensure quick detection and response to any potential threats. This minimizes the risk of data loss or corruption during migration, ensuring that the data remains intact and accurate.
Compliance with regulatory requirements
Many industries are subject to strict regulatory requirements regarding data protection and privacy. By achieving SOC 2 Type II and SOC 3 compliance, Help Desk Migration helps its customers meet these regulatory demands more easily. This is particularly beneficial for companies operating in highly regulated sectors, where compliance failures can result in severe penalties and reputational damage.
Commitment to continuous improvement
Achieving SOC 2 Type II and SOC 3 compliance is not a one-time event but an ongoing commitment. Help Desk Migration will continue to undergo regular audits to ensure that we maintain and enhance our security practices. This dedication to continuous improvement reflects our core mission: to provide our customers with the most secure, reliable, and efficient data migration services available.
Help Desk Migration’s journey to SOC 2 Type II and SOC 3 certification
Data security during importing or exporting processes can’t be underestimated. At Help Desk Migration, we always strive to go the extra mile for our customers in terms of advancing migration services and security measures. Recently, we added SOC 2 Type II and SOC 3 certification to our security portfolio.
We developed new policies, refined procedures, and strengthened security measures. Our employees participated in regular training sessions to increase their security awareness.
We collaborated closely with Sensiba, our independent auditor, who meticulously examined every aspect of our security protocols. After intensive efforts and numerous improvements, we successfully achieved SOC 2 Type II and SOC 3 certification. This journey has deepened our commitment to security and continuous improvement.
SOC 2 and SOC 3 Compliance Achieved: Help Desk Migration’s Milestone in Data Security
At Help Desk Migration, we understand that our customers entrust us with their most valuable asset: their data. The achievement of SOC 2 Type II and SOC 3 compliance marks a significant enhancement to Help Desk Migration’s security portfolio. It is a testament to our unwavering commitment to data security and our proactive approach to addressing the evolving threats in today’s digital landscape.
Our customers can now enjoy even greater peace of mind, knowing that their data migration projects are handled with the utmost care and the highest standards of security. Be sure to test our migration service in a free trial and check how easy to import your data to the desired help desk, service desk, or CSV file.
Frequently Asked Questions
SOC 2 Compliance Type II is important for businesses because it demonstrates that an organization has implemented effective controls and safeguards to protect the confidentiality, integrity, and availability of customer data. Achieving SOC 2 Type II compliance enhances trust and credibility with customers, partners, and stakeholders, and it can be a competitive differentiator in industries where data security and privacy are paramount.
The five trust service principles of SOC 2 Type II Compliance are:
- The security principle refers to protecting system resources against unauthorized access. Implementing access controls, encryption, and monitoring to safeguard against data breaches and other security threats is essential.
- Availability ensures that a system's services are available for operation and use as agreed upon. It focuses on maintaining the system's performance and uptime to meet customer expectations and requirements.
- Processing integrity involves ensuring that system processing is complete, valid, accurate, timely, and authorized. This principle is vital for maintaining trust in the system’s ability to process data correctly and consistently.
- Confidentiality is about protecting sensitive information from unauthorized disclosure. This includes data encryption, access controls, and other measures to ensure that confidential data remains private and secure.
- The privacy principle addresses the collection, use, retention, disclosure, and disposal of personal information. It ensures that the organization adheres to established privacy policies and practices, protecting personal data from unauthorized access.
SOC 2 compliance ensures your organization handles customer data with care. Here’s a breakdown of what’s needed:
- Security: Protect systems from unauthorized access.
- Use strong access controls.
- Regularly update and patch systems.
- Encrypt data at rest and in transit.
- Monitor and log access and usage.
- Availability: Keep systems running smoothly.
- Have a disaster recovery plan.
- Implement redundancy.
- Monitor system performance.
- Plan for capacity and load balancing.
- Processing Integrity: Ensure data processing is accurate and authorized.
- Verify data accuracy and completeness.
- Implement quality control measures.
- Monitor processing activities.
- Establish clear policies and procedures.
- Confidentiality: Protect confidential information.
- Use encryption.
- Apply data masking and anonymization.
- Restrict access to confidential data.
- Audit access controls regularly.
- Privacy: Handle personal information responsibly.
- Implement privacy policies aligned with laws.
- Obtain consent for data processing.
- Allow individuals to exercise their privacy rights.
- Ensure secure data disposal.
Here’s how to get SOC 2 compliant:
- Understand Requirements:
- Learn about SOC 2 trust service criteria.
- Identify applicable criteria for your organization.
- Readiness Assessment:
- Conduct an internal review.
- Identify gaps in current practices.
- Develop a remediation plan.
- Implement Controls:
- Develop policies and procedures.
- Deploy technical controls like encryption and access management.
- Train staff on compliance requirements.
- Document Everything:
- Document all implemented controls.
- Keep policies and procedures accessible and updated.
- Hire a Qualified Auditor:
- Choose an experienced, independent auditor.
- Schedule the audit and prepare documentation.
- Conduct the Audit:
- Work with the auditor on the assessment.
- Provide evidence of compliance.
- Review the Audit Report:
- Review findings and the audit report.
- Address any issues or recommendations.
- Maintain Compliance:
- Regularly update controls.
- Continuously monitor systems and
- Prepare for annual re-assessments.
By following these steps, you can achieve and maintain SOC 2 compliance, ensuring the protection and integrity of your customer data.
SOC 2 Compliance differs from other compliance frameworks in its focus on controls related to data security, availability, processing integrity, confidentiality, and privacy, specifically for service organizations. Unlike frameworks like SOC 1 (which focuses on internal controls over financial reporting) or PCI DSS (which focuses on credit card data security), SOC 2 is broader in scope, addressing a wider range of organizational controls related to the security, availability, processing integrity, confidentiality, and privacy of data.
Common challenges faced during SOC 2 Compliance include:
- Defining the scope and boundaries of the system under review.
- Identifying and implementing appropriate controls to meet the trust service principles.
- Documenting policies, procedures, and evidence of control effectiveness.
- Managing third-party vendor risks and dependencies.
- Navigating the complexities of audit preparation and engagement.
SOC 2 applies to service organizations that provide services like data hosting, cloud computing, Software as a Service (SaaS), managed IT services, and other services involving the processing or storing of customer data. These organizations typically include technology companies, data centers, IT service providers, and others where data security and privacy are critical.
SOC 2 compliance is not legally mandatory, but customers, partners, or regulatory bodies may contractually require it. Many organizations pursue SOC 2 compliance to demonstrate their commitment to data security and privacy and to meet their stakeholders' expectations.
A SOC 2 audit includes an examination of an organization's controls and processes related to the trust service principles. This examination typically involves:
- Reviewing documentation such as policies, procedures, and system configurations.
- Testing the effectiveness of controls through inquiry, observation, inspection, and re-performance.
- Assessing the design and operating effectiveness of controls to ensure they meet the criteria specified by the trust service principles.
- Providing a report detailing the auditor's findings, conclusions, and recommendations for improvement.
As part of the American Institute of CPAs’ Service Organization Control reporting platform, SOC 2 compliance comes under the spotlight, assessed through two distinct lenses: SOC 2 Type I and SOC 2 Type II reports.
- Type I reports delve into the intricacies of the service organization's system(s) and evaluate the design of controls for their suitability.
- Type II reports build upon the foundation of Type I, expanding to assess the operational effectiveness of these controls.
These reports serve as guardians of your customers’ data integrity, assuring compliance with standards and showcasing robust processes and controls to tackle risks head-on.
For entities mandated to showcase continual SOC 2 compliance, venturing into the realm of Type II reports proves invaluable. Regarded as the pinnacle, a Type II report illustrates the sustained efficacy of security measures over time, not just a fleeting moment.
However, if immediate SOC 2 compliance is the order of the day—perhaps constrained by timelines—Type I reports offer a swift solution. They can later serve as a stepping stone towards transitioning to Type II reports, laying a solid groundwork for the journey ahead.
Despite their akin titles, SOC 1 and SOC 2 diverge significantly in standards and objectives. While SOC 2 caters to aiding technology service providers and SaaS enterprises in safeguarding sensitive systems and data, SOC 1 is tailored to assist organizations in ensuring the efficacy of their internal controls concerning the management of customer financial data. Meanwhile, SOC 3, a complementary report to SOC 2, encapsulates similar information but is structured for public presentation, catering to a broader audience.
SOC 3 stands for System and Organization Controls 3. It’s a general-use compliance report that summarizes how a service organization meets key standards for security, availability, processing integrity, confidentiality, and privacy. The report is based on the same Trust Services Criteria as SOC 2 and serves as a public-facing validation of an organization’s commitment to protecting customer data.
SOC 3 isn’t better or worse—it serves a different purpose. SOC 2 offers detailed insights into a company’s controls and testing procedures, making it ideal for internal reviews or regulated industries. SOC 3 provides a high-level summary that’s designed for public distribution, helping organizations build trust with customers, partners, and stakeholders.
A SOC 3 report includes the following key elements:
- Auditor’s opinion – a professional assessment of control effectiveness
- Management assertion – confirmation from the organization’s leadership
- System description – a summary of the services evaluated
It confirms that controls related to security, availability, processing integrity, confidentiality, and privacy are in place and operating effectively over time.
While both follow the same audit standards, the reports differ in scope and usage:
- Detail level: SOC 2 is highly detailed; SOC 3 is a summary.
- Audience: SOC 2 is shared privately; SOC 3 is public-facing.
- Purpose: SOC 2 supports audits and vendor reviews; SOC 3 builds external trust.
- Report type: SOC 2 can be Type I or II; SOC 3 is always Type II.
Each plays a unique role in demonstrating an organization’s security commitment.